Introduction
I recently completed my degree in cybersecurity, and like every degree program, it included the daunting task of writing a dissertation. In my case, I enjoyed the journey and research because I chose a topic that fascinates me beyond my professional role and aligns with my personal projects: securing communications. Creating highly complex and secure communication systems is deeply satisfying, as the end result is a form of communication that cannot be censored, intercepted, or compromised, thereby protecting individual privacy.
For my dissertation, I focused on secure communication over radio, a critical concept since the pre-World War I era when Guglielmo Marconi pioneered wireless communication via radio waves. A significant turning point in history was the development of the Enigma machine during World War II, which highlighted the importance of encryption. Since then, encryption has become integral to nearly all forms of communication.
However, like the Enigma machine, modern encryption methods are not infallible and can be vulnerable to attacks, such as the "store now, decrypt later" strategy. With the continuous advancements in supercomputing, traditional encryption algorithms are beginning to show their age. While they remain effective against current supercomputers, their future resilience is uncertain. This underscores the need to implement post-quantum encryption, an additional layer of security designed to resist decryption by quantum computers, significantly enhancing protection against future threats.
Post-quantum encryption algorithms
Numerous post-quantum encryption algorithm designs exist, but my favorite is the Kyber concept, which uses lattice-based equations as a key encapsulation mechanism (KEM). This approach was selected by the National Institute of Standards and Technology (NIST) in 2022 as a standard for post-quantum key encapsulation. Kyber operates by utilizing two lattices that are mathematically related but differ in complexity. The "basic" lattice serves as the private key, which is computationally straightforward for a computer to use to return to the origin point. In contrast, the "complex" lattice acts as the public key, which is easy to use for encryption but practically impossible to reverse-engineer to find the origin. The structural difference between the two lattices is so significant and complex that it would take trillions of years to compute, ensuring robust security against quantum attacks.
Lattices can range from simple to highly complex, often requiring computers to calculate them. They can be visualized as 2D or 3D diagrams, but the Kyber design employs algebraic lattices defined over high-dimensional mathematical structures, specifically polynomial rings in the context of the Module-LWE (Learning with Errors) problem. While this may mean nothing to a laymen like me, basic lattice encryption can be explored using 2D visualizations to intuitively understand how lattices function.
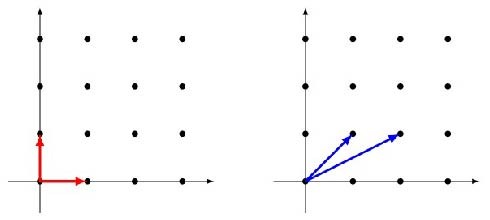
On the left is the "basic" private key, which can easily return to the origin from a given set of coordinates. In contrast, the "complex" public key on the right is much harder to trace back to the origin from a set of coordinates. Now imagine this lattice space extended to a million dimensions, where the two blue lines on the right represent billions of points apart from each other, yet mathematically remain equivalent to the basic red lines on the left.
Using a hybrid symmetric encryption
Symmetric Hybrid encryption can be achieved by combining AES-256 (Advanced Encryption Standard with a 256-bit key), a symmetric encryption algorithm, and Kyber, a lattice-based post-quantum key encapsulation mechanism (KEM), to secure communication between two points. In this approach, two individuals who have met in person exchange their Kyber public keys securely. These keys are then used to establish a shared secret through Kyber's KEM, which is resistant to quantum attacks. This shared secret is subsequently employed to symmetrically encrypt the communication data using AES-256, providing high-speed and robust encryption.
This method requires that both parties know each other's public keys beforehand, as the in-person exchange is essential for securely initiating the process. Without this prior key exchange, the hybrid system cannot be effectively implemented, as Kyber relies on the pre-shared public keys to generate the shared secret, which AES-256 then uses for encryption.
Using a hybrid asymmetric encryption
Asymmetric hybrid encryption can be achieved by combining RSA (Rivest-Shamir-Adleman), an asymmetric encryption algorithm, and Kyber, a lattice-based post-quantum key encapsulation mechanism (KEM), to secure communication between two points. In this approach, two individuals who have met in person exchange their RSA public keys securely. These keys are then used to establish a shared secret through RSA, which is resistant to classical attacks when using sufficiently large key sizes. This shared secret is subsequently employed to symmetrically encrypt the communication data using AES-256, providing high-speed and robust encryption.
Hardware
A variety of hardware solutions are available, ranging from designing custom PCBs to utilizing plug-and-play components. For this dissertation, I opted for a practical approach by purchasing two LoRa hat components and two Raspberry Pi Zero W devices. If I were to expand this project further, I would design compact, small-form-factor devices featuring screens and keyboards for mobile use. For now, however, I am focusing on using a Raspberry Pi to host a web app that communicates with the hardware.
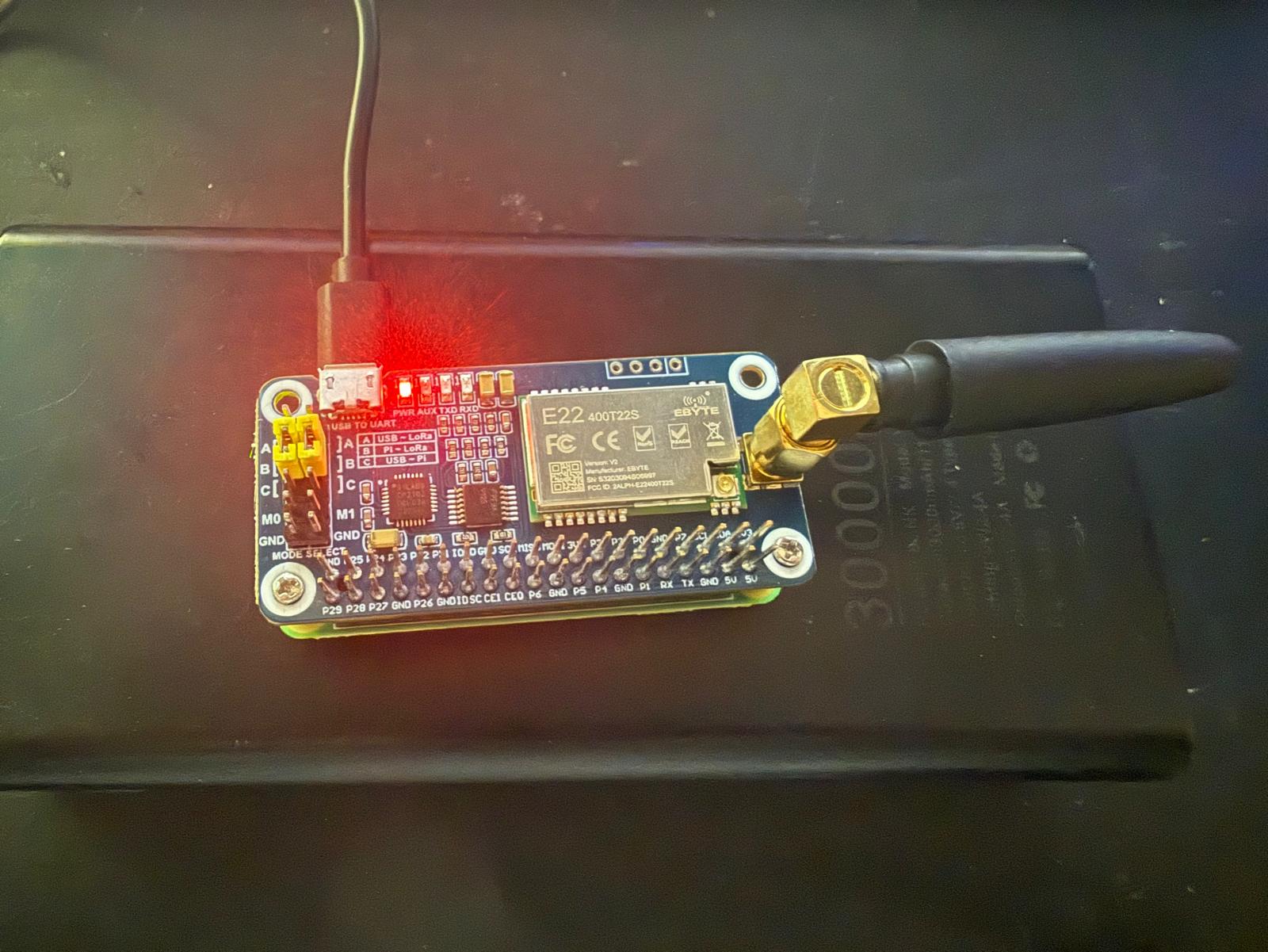
To complement the current setup, I plan to conduct further testing with the prototype to ensure reliable communication between the devices. Given my time constraints and uncertain future involvement, I will avoid complex modifications and focus on optimizing the existing Raspberry Pi and LoRa hat configuration. This includes fine-tuning the web app’s connection to the hardware and documenting the prototype’s performance, providing a solid reference for any potential future exploration by others.
Software
To enable communication, we need a method to enter messages, add contacts, and perform related tasks, which falls under the realm of software. Since there is no ready-made solution for this, we have the opportunity to develop it ourselves. I am inclined toward creating a web app, allowing users to access it on their mobile phones by visiting a local address. This would typically require internet access; however, we can transform the Raspberry Pi into a Wi-Fi access point and connect directly from the phone, enabling all communications to occur offline.
To achieve this, I have chosen to use my preferred framework, SvelteKit—the same framework used to build this site. With SvelteKit, we can leverage TypeScript and Node.js to communicate directly through the GPIO pins using an NPM package called onoff. By reviewing the user manual and spec sheet for the LoRa hat I purchased, we can determine how to interface with the LoRa hat via the GPIO pins.